Cryptology
History of Cryptology
Cryptology is the study of hidden writing. It comes from the Greek words Kryptos, meaning hidden, and Graphen, meaning to write. Cryptology is actually the study of codes and ciphers. Concealment messages aren’t actually encoded or enciphered, they are just hidden. Invisible ink is a good example of a concealment message.
A code is a prearranged word, sentence, or paragraph replacement system. Foreign languages are just like secret code, where the English word “hi” is represented as the word “Hola” in Spanish, or some other word in another language. Most codes have a code book for encoding and decoding.
The name cipher originates from the Hebrew word “Saphar,” meaning “to number.” Most ciphers are systematic in nature, often making use of mathematical numbering techniques. One example of a cipher is the Spartan stick method.
The Spartans enciphered and concealed a message by using a scytale, a special stick and belt. The encipherer would wrap the belt around the stick and write a message on it. The belt was then unwound from the stick and sent to another person. Using a stick of similar size, the decipherer would wrap the belt around the stick to watch the secret message appear. If a stick of the wrong size appeared the message would be scrambled. Try this with 2 or 3 pencils bound together to make a stick, a long strip of paper, and another pencil for writing.
Julius Caesar used a simple alphabet (letter) substitution, offset by 3 letters. Taking the word “help” you would move ahead in the alphabet 3 letters to get “jgnr.” This worked for a while, until more people learned to read and studied his secret cipher.
Gabriel de Lavinde made cryptology a more formally understood science when he published his first manual on cryptology in 1379. A variety of codes and mechanical devices were developed over the next few centuries to encode, decode, encipher, and decipher messages.
In the 1600’s Cardinal Richelieu invented the grille. He created a card with holes in it and used it to write a secret message. When he was done he removed the card and wrote a letter to fill in the blanks and make the message look like a normal letter. The grille proved to be difficult to solve unless the decoder had the card which created the encrypted message.
In 1776 Arthur Lee, an American, developed a code book. It wasn’t long before the US army adopted a code book of their own for use in the military.
The Rosetta Stone (black basalt), found in Egypt in 1799, had a message encrypted on its surface in three different languages! Greek, Egyptian, and Hieroglyphics messages all said the same thing. Once the Greek and Egyptian languages were found to have the same message the Hieroglyphics language was deciphered by referencing each letter to a symbol!
Morse Code, developed by Samuel Morse in 1832, is not really a code at all. It is a way of enciphering (cipher) letters of the alphabet into long and short sounds. The invention of the telegraph, along with Morse code, helped people to communicate over long distances. Morse code can be used in any language and takes only 1 to 10 hours of instruction/practice to learn! The first Morse code sent by telegraph was “What hath God wrought?”, in 1844.
During WWI Karl Lody sent the following telegram “Aunt, please send money immediately. I am absolutely broke. Thank heaven those German swine are on the run.” The clerk realized that this message didn’t make any sense and forwarded it to the proper authorities who found Karl Lody guilty of espionage (spying). Can you see why his message must be a secret code or cipher? Why doesn’t it make any sense?
In 1917, during WWI, the US army cryptographic department broke the code of the Germans. The code was actually stolen by Alexander Szek, a man working in a radio station in Brussels at the time. Unknown to the Germans, Szek was an English sympathizer and was stealing a few code words every day. When the Zimmerman telegraph was sent in 1918, asking Mexico to go to war against the United States, the US army cryptography department broke the code and decoded the telegraph.
The Germans learned from this experience and changed their codes. But the British were able to obtain copies of new code books from sunken submarines, blown up airplanes, etc., to continue breaking the new codes. By WWII navy code books were bound in lead to help the code books sink to the bottom of the ocean in the event of an enemy takeover.
The little known native Indian language of the Navajo was used by the US in WWII as a simple word substitution code. There were 65 letters and numbers that were used to encipher a single word prior to the use of the Navajo language. The Navajo language was much faster and accurate compared to earlier ciphers and was heavily used in the battle of Io-jima.
The Germans in WWII used codes but also employed other types of secret writings. One suspected spy was found to have large numbers of keys in his motel room. After inspecting the keys it was found that some of the keys were modified to unscrew at the top to show a plastic nib. The keys contained special chemicals for invisible ink! However, codes and secret ink messages were very easily captured and decoded.
The Germans, responsible for much of the cipher science today, developed complex ciphers near the end of WWII. They enciphered messages and sent them at high rates of speed across radio wave bands in Morse code. To the unexpecting it sounded like static in the background. One gentleman tried to better understand the static and listened to it over and over again. The last time he played his recording he forgot to wind his phonograph. The static played at a very slow speed and was soon recognized as a pattern, Morse code!
The invention of computers in the 20th century revolutionized cryptology. IBM corporation created a code, Data Encryption Standard (DES), that has not been broken to this day. Thousands of complex codes and ciphers have been programmed into computers so that computers can algorithmically unscramble secret messages and encrypted files.
Some of the more fun secret writings are concealment messages like invisible inks made out of potato juice, lemon juice, and other types of juices and sugars! Deciphering and decoding messages take a lot of time and be very frustrating. But with experience, strategies, and most of all, luck, you’ll be able to crack lots of codes and ciphers.
Strategies for Deciphering
The first things you should do is
get organized!
Compile a list of known codes and cipher methodologies that you can use on secret messages. Once you have tried all the methods you know of, use a hit and miss method, trial and error. The structure of the English language enables cryptologists to see patterns that emerge from normal messages. Just by looking at this paragraph of text, or playing Wheel of Fortune, you can figure out which letters are most common.
Vowels and spaces are the most frequent in the English language. A few constants, such as “S, T, N, etc.” are more common than others. Finally, a few known bigrams (2 letters), such as “ll, ee, ss, etc,” are more common than others. By recognizing patterns in ciphers you can often guess what the letters are decipher the message. The computer application “Cryptogrammer” teaches you how to decipher this way. Ask your instructor if you are interested in playing Cryptogrammer.
Most Common Letters
- E
- T
- A, O, N, R, I, S
- H
- D, L, F, C, M, U
- G, Y, P, W, B
- V, K, X, J, Q, Z
Bigram Frequency
In order from most common to least common:
TH, HE, AN, RE, ER, IN, ON, AT, ND, ST, ES, EN, OF, TE
Bigram Same Letter Frequency
In order frommost common to least common:
LL, EE, SS, OO, TT, FF, RR, NN, PP, CC, MM, GG
Trigram Frequency
THE, ING, CON, ENT, ERE, ERS, EVE, FOR, HER, TED, TER, TIO, VER
Intial Letters
T, A, O, M, H, W, C, I, P, B, E, S
Second Letters
H, O, E, I, A, U, N, R, T
Third Letters
E, S, A, R, N, I
Final Letters
E, T, S, D, N, R, Y, G
*More than 50% of English words end with “E.”
*More than 50% of English words start with T, A, O, S, or W.
Frequency Tables for Deciphering
It’s a good idea to create a table of the counts
for letters of the alphabet, bigrams, trigrams, and initial and ending letters to see how many times a certain letter(s), number(s), or symbol(s) from an encrypted message occurs. The highest occurance of a single letter/number/symbol is most likely to be “E” as seen in the frequency table above. The most common 2 letter/number/symbol bigram is likely to be “TH.” If you can place a few likely letters you will often see a few short words, like “THE” appear.
Once words start to appear you’re on to something. See if there is an easy pattern to get the rest of the letters. If not, continue
analyzing frequency tables
to decode the rest of the letters.
Use trial and error
and replace letters/numbers/symbols with different letters until more words begin to appear. Try this method on the simple cipher below. Can you figure out what the encrypted message says?
Wpxfmt bsf uif nptu dpnnpo mfuufs
Letter, Syllable, & Word Frequencies
When trying to decipher an enciphered message you may find letter and syllable frequencies to be helpful. The most common letters, numbers, or symbols used in the message are likely to be the most common letters of the plain alphabet, spaces, or punctuation marks. By identifying patterns and the frequency of letters, syllables, two and three letter words, etc, you can better decipher secret messages.
Let’s say you get an enciphered message reading:
NMO GRBTF MZW ZTGZCW POOV NMO WXDO; ZVF NMOBO MZW ZTGZCW POOV ZW DSUM KRRF QRBNSVO ZW PZF XV XN
What two and three letters are used more than once? What is the most common letter? Which letter is most likely a vowel like the letter “e”? The deciphered answer is:
THE WORLD HAS ALWAYS BEEN THE SAME; AND THERE HAS ALWAYS BEEN AS MUCH GOOD FORTUNE AS BAD IN IT.
-Quote by Machiavelli, “Discorsi”
Do you see how the word “THE” is represented by “NMO”? “O” is one of the most frequent letters because it is actually the letter “E.” The following assignment will help you to identify your own frequency charts to use when deciphering messages like the one above.
Use the reading attached to this document to identify a frequency count for:
- letters a-z
- two and three letter words (an, of, etc.)
- syllables (ll, tt, etc.)
- first character of each word (like how many words start with “w”, etc.)
- punctuation marks (,?:”!…)
Perhaps you should start by writing out a list of each frequency assignment above. Then count the frequency for each assignment, a-e, as shown above. When you are all done, analyze the results and write out an ordered list of frequencies for each assignment above.
The report for assignment a may look something like:
Total Characters = 354
Letter Frequency
E 135
R … 122 ..
Reading Sample
5 Building Blocks of Good Design
1. Proportion of a Single Item
How a single item is displayed. As an example: Rather than using a square to outline text or graphics use a proportional rectangle that is pleasing to the eye. The Greeks used a rectangle, now called the golden rectangle, that used proportions of approximately 1 to 1.618. Photographs are now printed on paper in a standard 3X5″ because it is a shape that is fairly close to that of a golden rectangle, a shape that is more pleasing to the eye.
2. Proportion of a Relative Sizes
How two or more objects on a page compare to one another with respect to your message. As a general rule, larger items on a page are usually the more important items in your overall message.
3. Balance
It’s important to maintain a balance of size and position of objects to provide the reader with a clear and interesting message. The visual center (golden mean) of a 8.5X11″ paper is slightly above and to the left of the mathematical center. It’s often a good idea to place the dominant object in the visual center or visual starting point of your document. Consider the visual weight of each object based on the objects properties: size, color, pattern, angle of display. Making use of white space to separate items can sometimes have a dramatic and effective roll upon the acquisition of balance.
4. Contrast
A paper without contrast is like a speech in monotonic presentation. Contrast adds to the importance of items, gathers interest, and spices up your document. Contrast is often added to documents by varying the type used for the text (font, style, size, color, etc.). Use of graphics, such as graphs, tables, photographs, borders, and illustrations are another method for providing contrast. Be careful not to overdo the contrast, creating a busy and irritating document that shouts at you rather than captures your interest in a pleasing way.
5. Rhythm
How are items placed on your document? Are you leading the reader’s eyes around the document, or is it unorganized and hard to follow? Design your document to force the reader’s eye to move up and down, left to right, in a circle, etc., as needed to capture the reader’s interest and clearly direct them towards skimming and scouring modes of reading.
Invisible Ink & Mirror Images
Invisible Ink
Invisible ink has been used to conceal secret messages for a long time. You might remember the spy that used keys to hide invisible ink chemicals? Well the science of creating invisible messages has come a long way in the last 100 years. Professional scientists have developed invisible inks that are difficult to detect, even by the professional spy. If you’d like to experiment with invisible ink you can use some simple materials from home:
Invisible Ink Ingredients – Developed by Brady Schaures
1/4 cup white grapefruit juice
1/3 tsp. lemon juice
Pinch of sugar
Directions
Use a Q-tip to dip into the invisible ink and write you message on white paper. After the message dries you can use a hot iron, burning match, or lighter to burn the ink on the paper. CAUTION – Don’t try this at home unless you have direct adult supervision. It is recommended that you use an iron to avoid the chance of fire.
The paper will turn brown and eventually burn up if you overheat the paper. The secret is to heat up the paper a little, see if the message has appeared, and then try again until you can see the message on the paper.
You may want to experiment with other liquids around the house until you can create an invisible ink that can’t be seen on paper until it is burned. Other juices are a great way to write invisible ink on colored paper as well. Try orange juice, cranberry juice, and others.
Mirror Images
By making use of a computer you can easily create images that are backwards, only readable when seen in a mirror. Simply write your message and use painting or drawing tools to flip the message horizontally. Then print your message and hold it up to a mirror. The message below has been flipped horizontally and can be read in a mirror.
What is the message above?
Flip the text horizontally once you’re ready to make it a mirror image.
Camouflage Crayons
Another way to hide a message is to use crayons. Use a pencil to write a message as lightly as possible on some paper. Then use crayons to cover up the message. If possible, draw a picture that is unsuspecting and looks normal. To see the secret message use a sharp knife or razor blade to scrape off the crayon marks. Be careful when handling the knife!
*Histiaeus, in 500 B.C., wrote a secret message on a slave’s head, waited for his hair to grow back, and sent his slave cross enemy lines. When his head was shaved the message appeared!
Cipher Clocks
Cipher clocks can be made to correlate the value of a letter to another letter, number, or symbol. Start by making a linear list of cipher values. See the examples below:
Offset by four: Counting the letter you start with, count forwards 4 letters.
A B C D E F G H I J K L M N O P Q R
D E F G H I J K L M N O P Q R S T U
S T U V W X Y Z
V W X Y Z A B C
Letters represented by numbers:
A B C D E F G H I J K L M N O P
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16
Q R S T U V W X Y Z
17 18 19 20 21 22 23 24 25 26
Random letter substitution:
A B C D E F G H I J K L M N O P
D E F G H I J K L M N O P Q R S
Q R S T U V W X Y Z
T U V W X Y Z A B C
Random letters substituted by numbers:
A C B Z R T W N O M L J P U E
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15
I D K F
16 17 18 19
V G H S X Y Q
20 21 22 23 24 25 26
Making Your Cipher Clock
Once you have a cipher you like, make a cipher clock from two circular pieces of paper. Place the smaller piece of paper on top of the larger piece. Then write your alphabet, with desired punctuation on one piece of paper, your cipher equivalents on the other. Make sure you space all the letters out equally so that the cipher letters/symbols align with the alphabet as you turn your clock. Put a paper faster in the middle and start en/deciphering!
Larger Piece of Paper Smaller Piece of Paper Completed Clock!
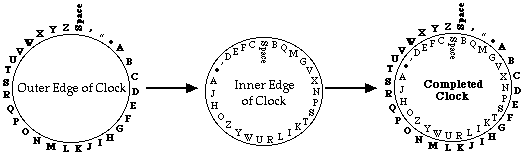
Can you figure to how to have more than one cipher on a cipher clock?
Matrix Ciphers
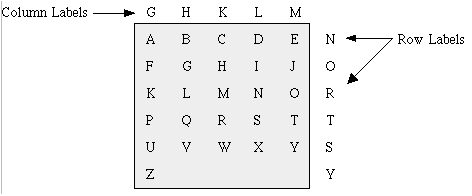
A matrix is something that resembles an array, such as the regular formation of the letters of the alphabet written into columns and rows. By making use of a matrix, similar to references in an “X, Y” graph, a cipher can be created. The matrix below uses column and row labels to create a secret cipher.
Since the letters are written into a matrix, the letters for column and row labels can be combine to identify the location of a letter within the matrix. As an example, the letter “A” is in column “G,” row “N.” Thus, “A” could be written into an enciphered messages as “GN.” Look at the example below to see how the word “DOG” is enciphered using the matrix above.
Plain Message: D O G
Enciphered Message: LN MR HO
Can you make the matrix grid above a little harder? Think about the sequencing of letters, the number of possible matrix cipher values created by columns and rows references, and the number of rows or columns used.
Do you think it is possible to decipher a message encoded with the system above without having the matrix to refer too? How could you break the cipher system of another person’s matrix cipher? Make up your own matrix cipher and see if your friends can decipher the message!